
Cyber Hero
The essential cybersecurity toolkit for everyone

The essential cybersecurity toolkit for everyone
Cyber Hero is ideal for cybersecurity students, ethical hackers, penetration testers, developers, and IT professionals. Whether you're studying networking, conducting vulnerability assessments, or managing servers, Cyber Hero equips you with all essential tools right on your Android device. It's also great for educators and trainers looking for a mobile-ready teaching aid.
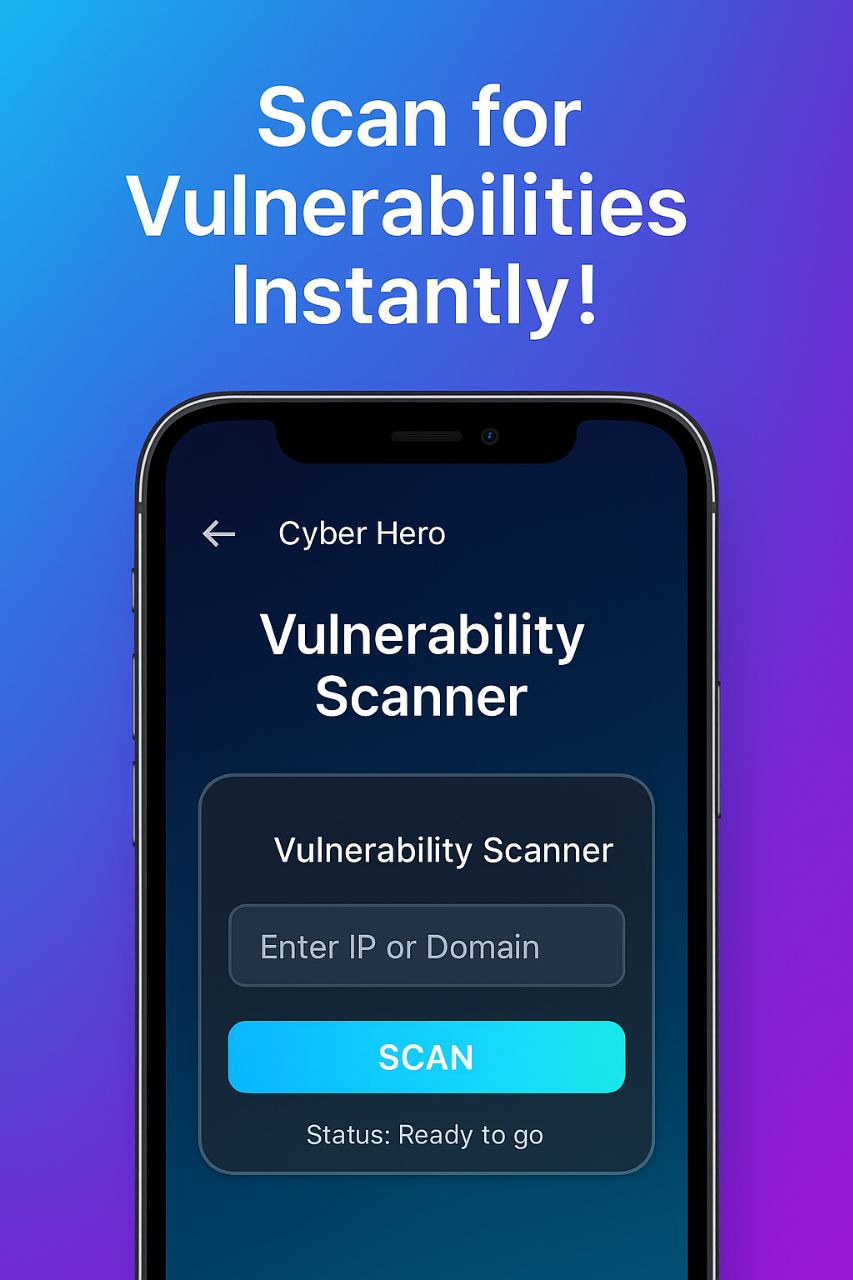
Cyber Hero operates 100% offline. All scans, lookups, and assessments are performed locally without sending any data over the internet. No user tracking, no server dependencies—just fast, secure, and private usage for professional environments and personal research.
Whether you're auditing your home Wi-Fi, conducting network scans in class, or doing real-world testing in the field, Cyber Hero is your reliable digital sidekick. Download the app now and experience cybersecurity tools that work seamlessly, even without an internet connection.
You can try it on desktopA Cyber Hero refers to ethical hackers or security professionals who defend systems, identify vulnerabilities, and protect organizations from cyber threats.
Example Tools:
Kali Linux (For ethical hacking)Metasploit (Exploitation framework)Mobile or desktop applications designed for hacking (ethical or malicious). Ethical versions help in security testing.
Popular Apps:
Termux (Android-based CLI for pentesting)AndroRAT (Malicious remote access tool)Tools that discover subdomains (sub.example.com) of a website, revealing hidden entry points.
Top Tools:
Sublist3rAmassFindomainUse Case:
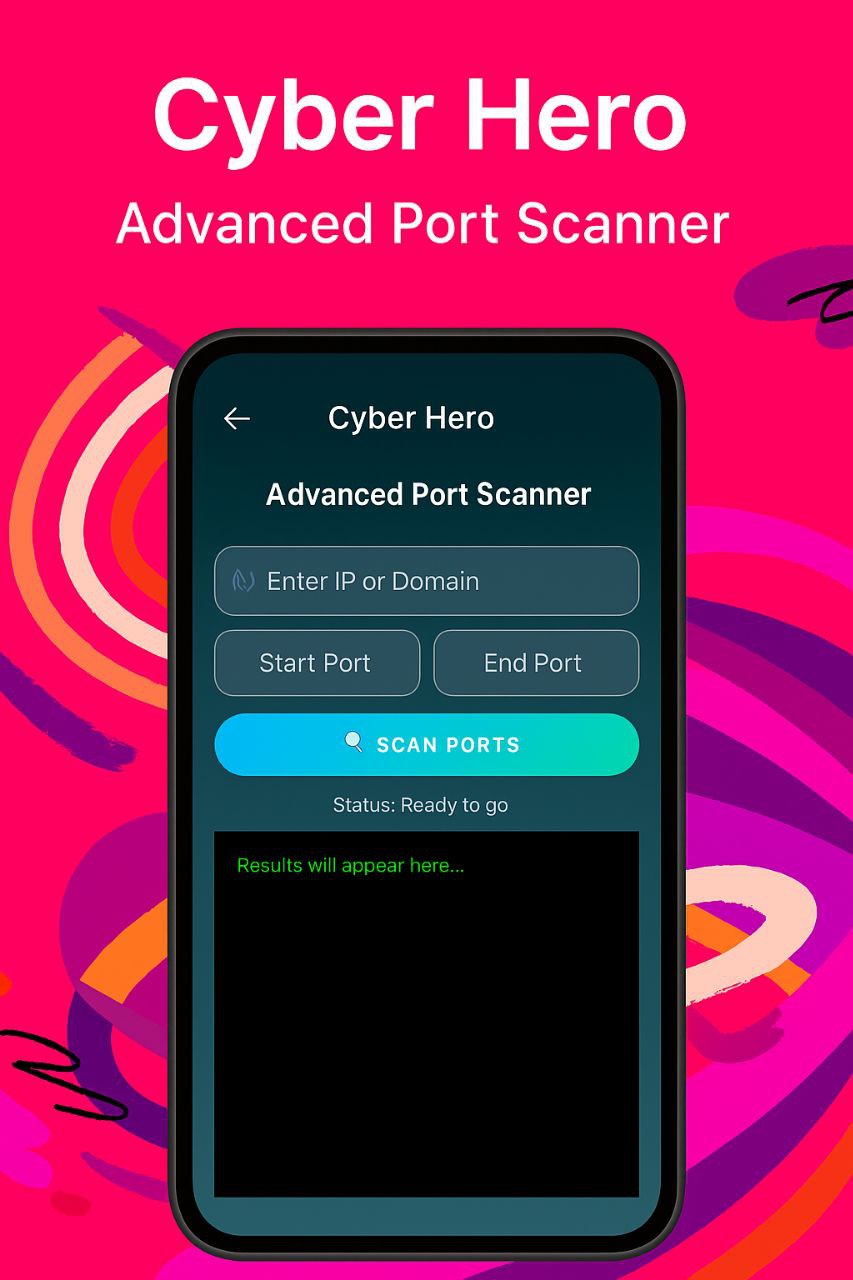
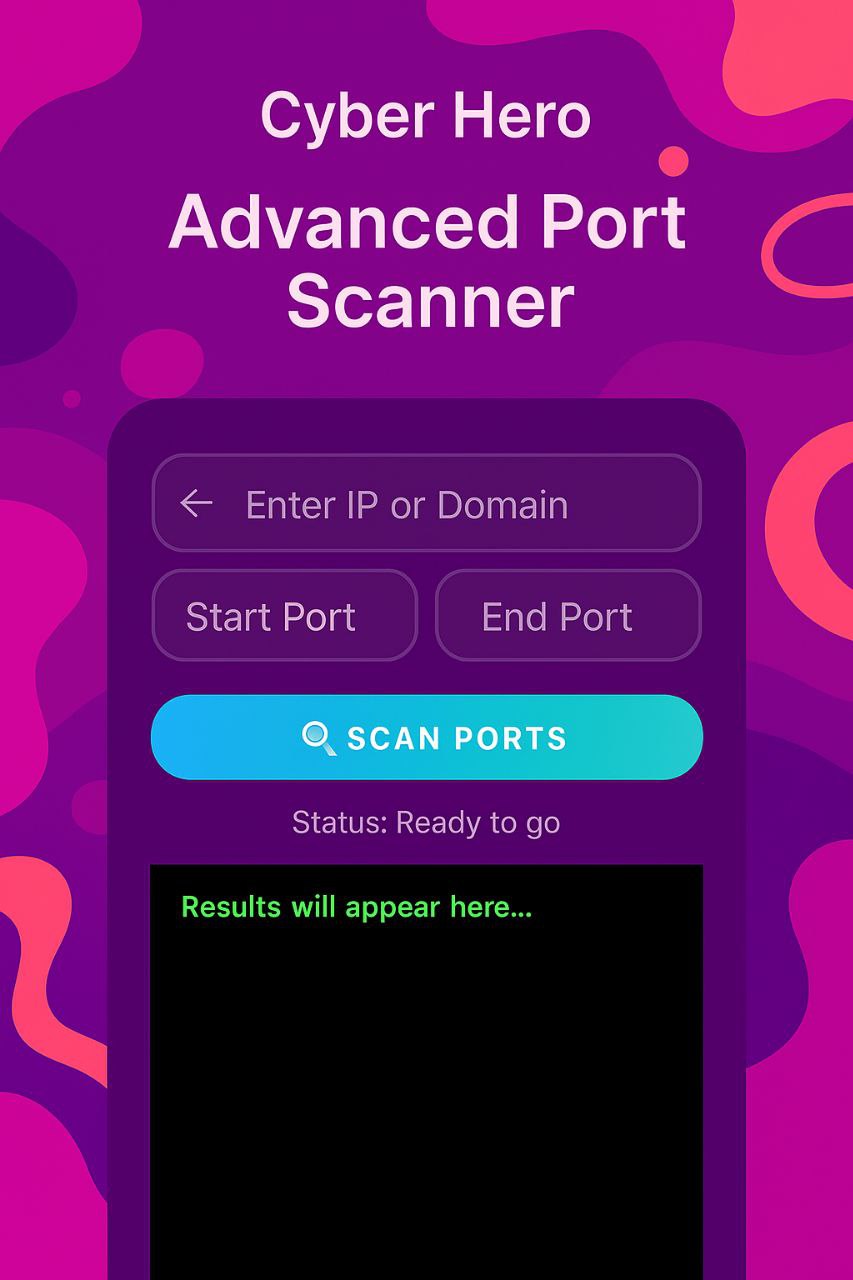
Identifies open ports on a target system to detect potential vulnerabilities.
Popular Tools:
Nmap (Industry standard)Masscan (Fast large-scale scans)Example Command:
Similar to port scanners but often includes additional features like service detection.
Tools:
Netcat (nc)Zenmap (GUI for Nmap)A vulnerability where an unused subdomain points to a deactivated service that attackers can claim.
Prevention:
Subjack or Takeover(Distributed Denial of Service) Overwhelms a target's server with fake traffic.
Types:
Mitigation Tools:
CloudflareAWS ShieldAll points (APIs, ports, subdomains) where an attacker could exploit a system.
Reduction Tactics:
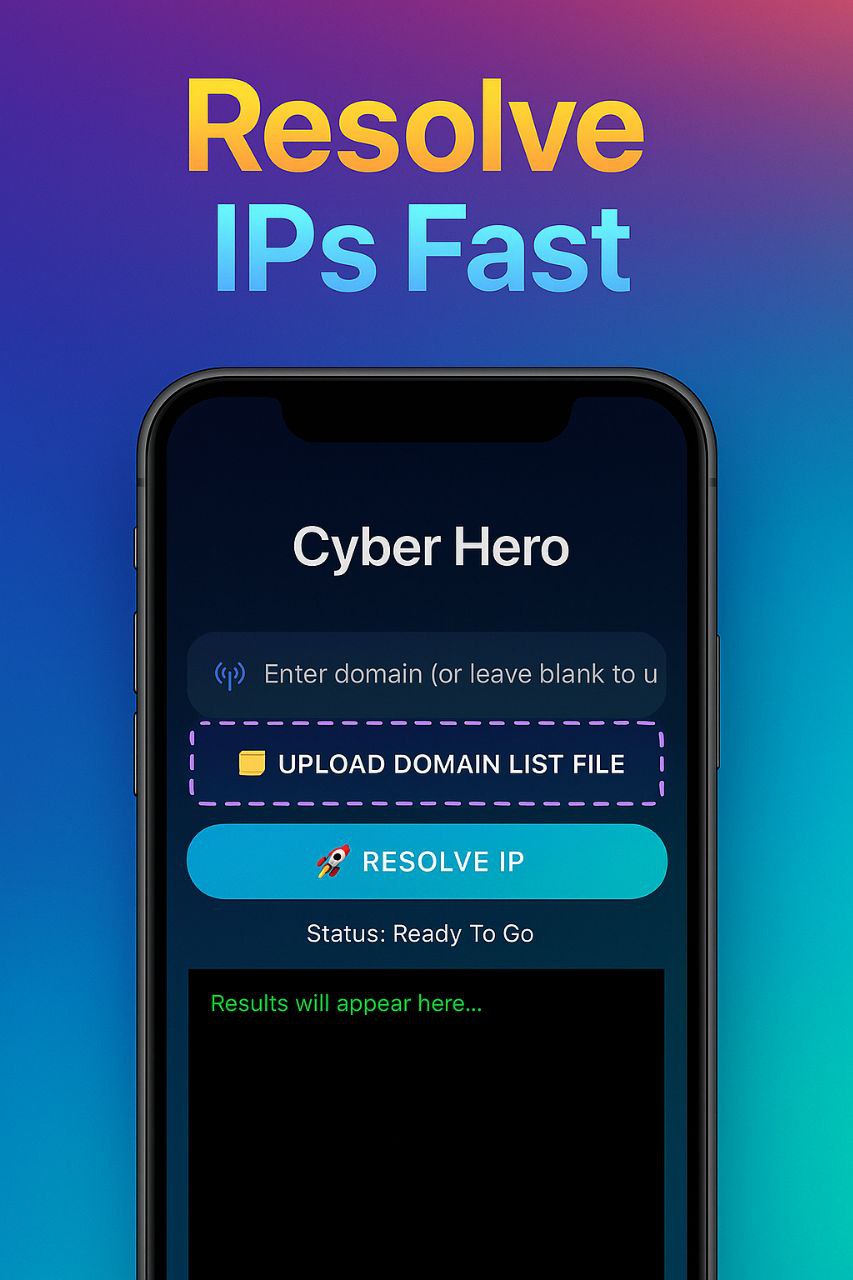
Tools that map domain names to IP addresses or provide geolocation details.
Tools:
DigWhoisIPinfo.ioExample Command:
Subdomain Finder → Port Scanner → Vulnerability Scanner).